Windows never ceases to amaze us with the possible vulnerabilities. If one gets a patch, another one will pop out of nowhere. One such vulnerability is the recent Printer vulnerability (CVE-2021-34481), also called Print Spooler vulnerability. It comes right after Microsoft fixed the PrintNightmare Vulnerability on Windows. You’ll need to disable the Print Spooler service, as a result.
The Print Spooler Vulnerability allows any hacker with physical access to your device to install any program, view and modify your files and data, and also create new accounts on your PC. The need for physical access to execute the code makes it less vulnerable but still could be a possibility of a hacker gets access to the physical system.
Microsoft hasn’t given any time frame regarding when this will be patched, but there’s a temporary workaround to get through it — Disable Print Spooler Service, just as Microsoft suggested.
In this guide, we’ll show you how to disable the Print Spooler on Windows to fix the Windows Printer Vulnerability. In addition to that, we’ll also show how to enable print spooler, once the vulnerability is patched.
How to Disable Print Spooler Service to Fix Printer Vulnerability on Windows
There are two methods to disable the Print Spooler service — The PowerShell method, and the Group Policy Editor method.

The PowerShell method stops printers from working both locally and remotely. Whereas Group Policy Editor method only stops printers from working remotely and you can still use them locally without internet access.
Before using any of these methods, make sure that you are protected against the PrintNightmare Vulnerability.
Method 1: Disable Print Spooler Service using PowerShell
You can use PowerShell to disable the Print Spooler service on your system. But you need to note that, you won’t be able to print anything using the printer (not even remotely).
However, not printing is better than suffering from attacks of hackers from the Printer vulnerability on Windows.
To disable Print Spooler service using PowerShell:
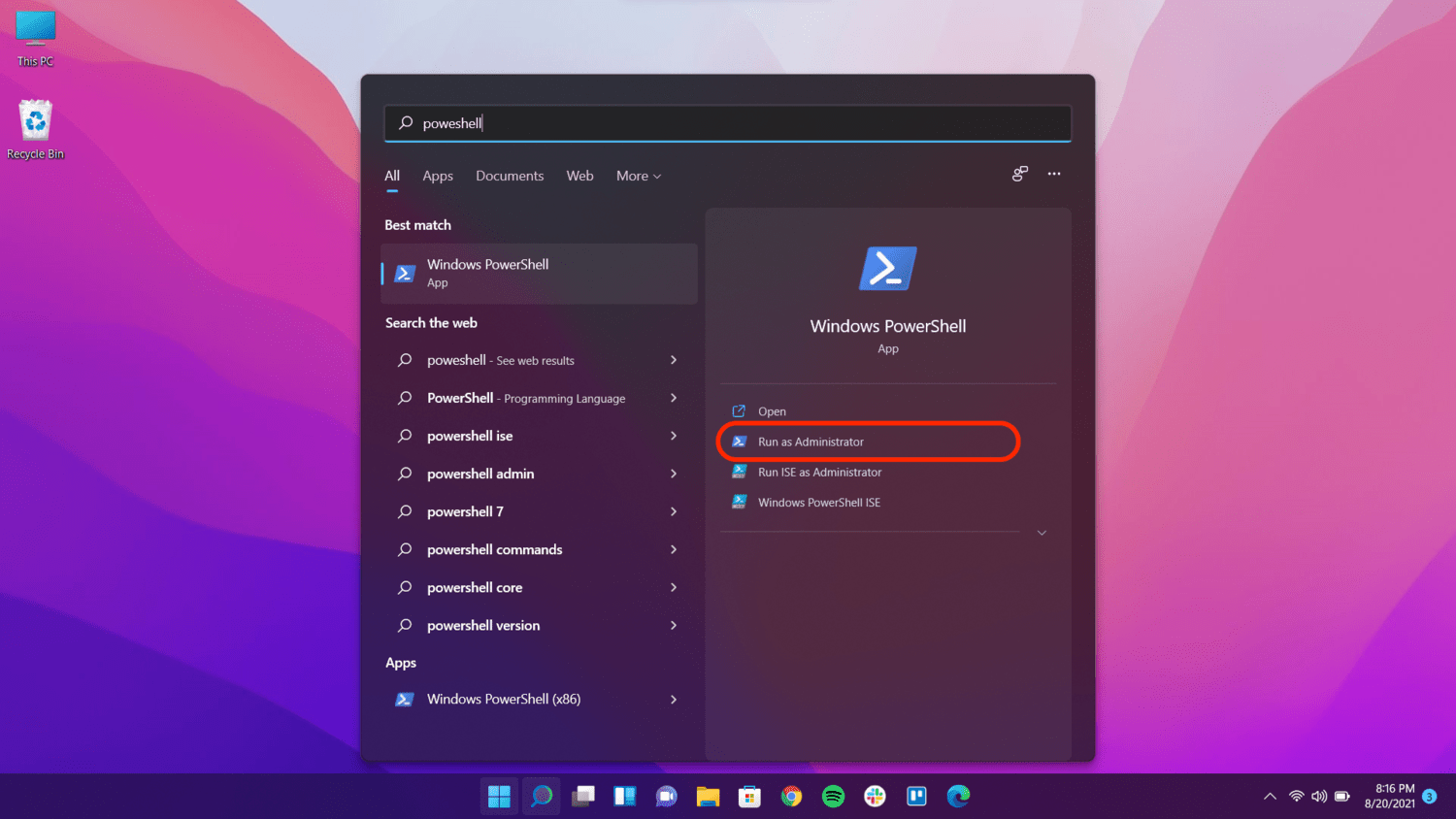
- Open the Start menu.
- Search for “PowerShell.”
- Right click on Windows PowerShell and select Run as Administrator.
- Type the following command and hit Enter key to stop the Print Spooler service:
Stop-Service -Name Spooler -Force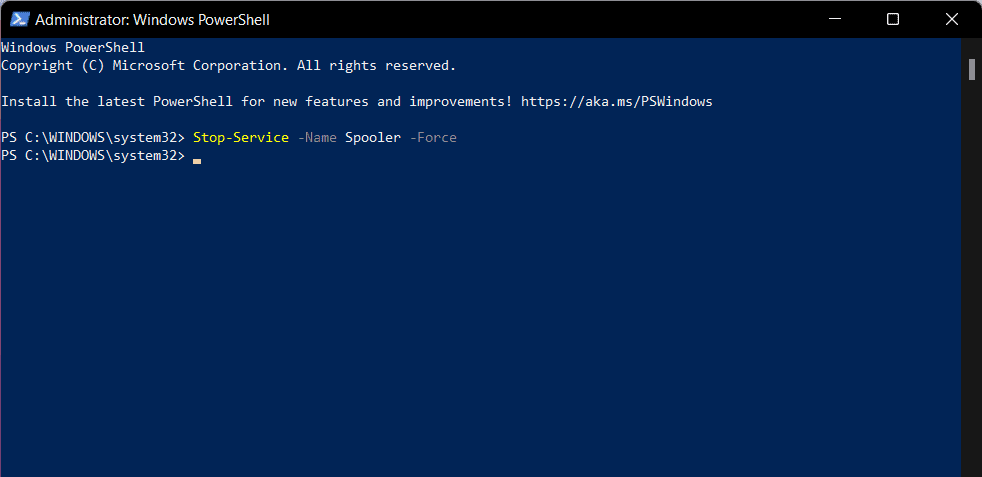
- Restart your computer for the changes to take effect.
This command will prevent the Print Spooler service from starting up when your system starts in order to get rid of the Print vulnerability on Windows. This will stop all printers connected to your computer from working – both locally and remotely.
Method 2: Disable Print Spooler Service with Group Policy Editor
If you want to use the printer locally and can sacrifice remote access to the printer; it’s best to use the Group Policy Method. This method is probably the best among the two. Since hackers usually go for remote access rather than local or physical access.
Note that this method won’t work if you’re running the Windows 10 Home Edition, but will work on other editions of Windows 10.
To disable the Print Spooler from Windows 10 using the Group Policy method:
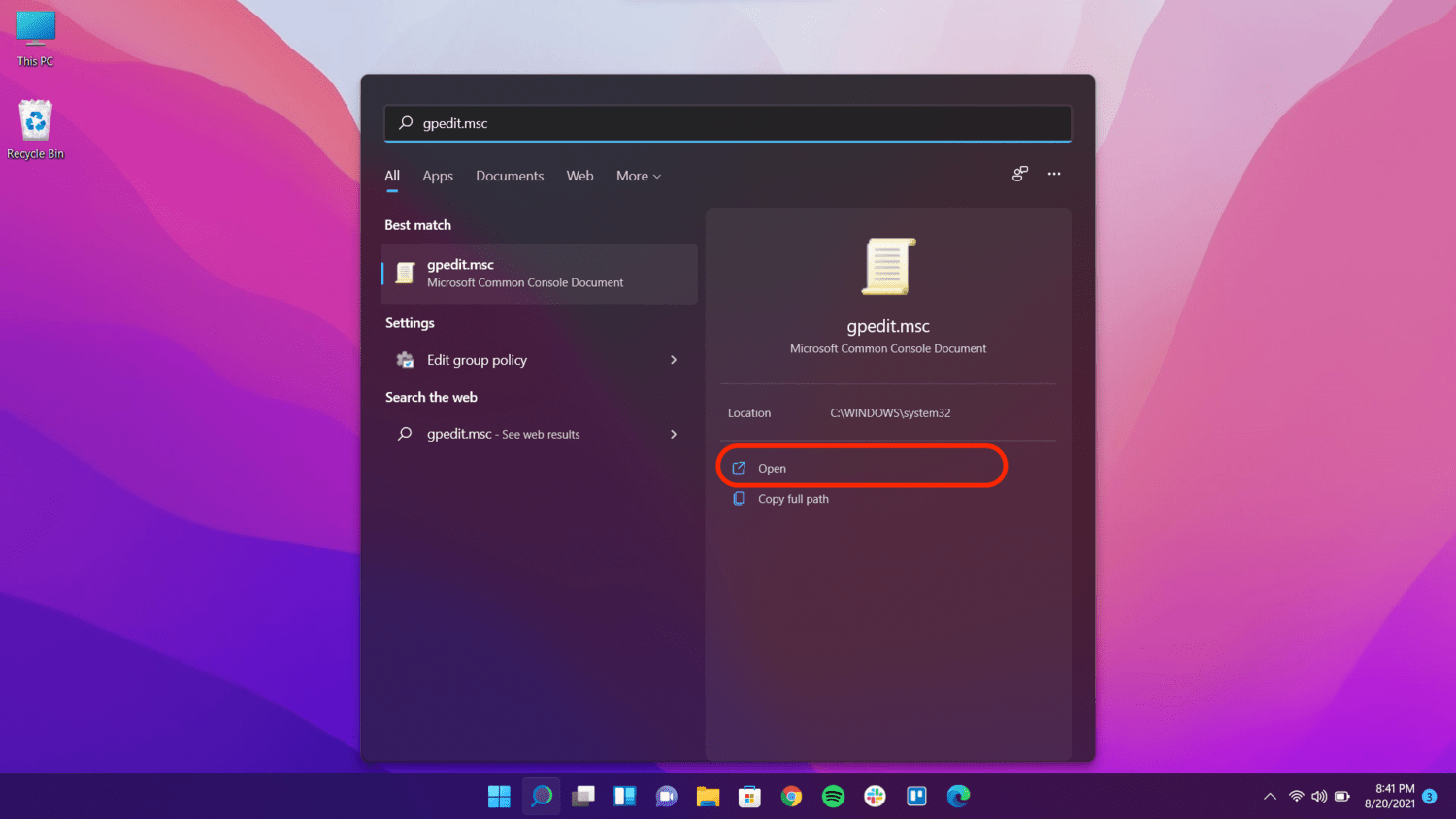
- Open the Start menu.
- Search with the term “gpedit”.
- Right click on “gpedit.msc” and select Run as Administrator option. (On Windows 11, the Run as Administrator option is not present, and thus, you can click on the Open directly).
- Navigate to the Computer Configuration > Administrative Templates > Printers.
- Scroll down a little, and double-click on the “Allow Print Spooler to accept client connections”.
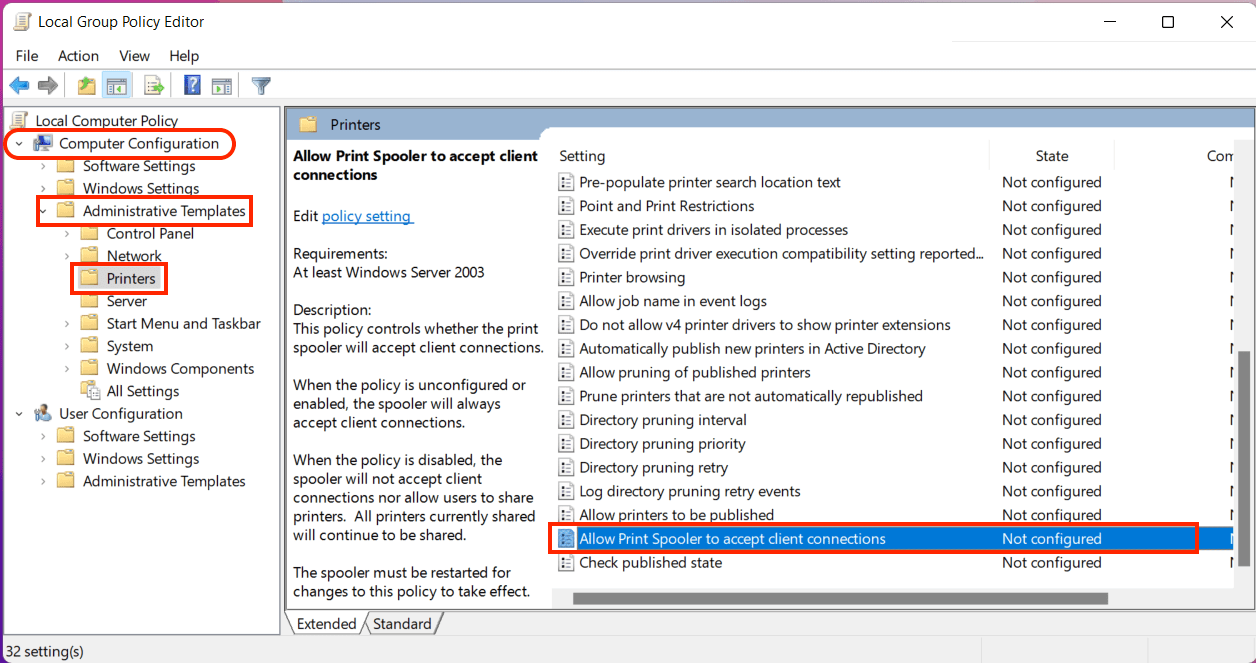
- Select the Disable radio button.
- Click on Apply and then hit the OK button.
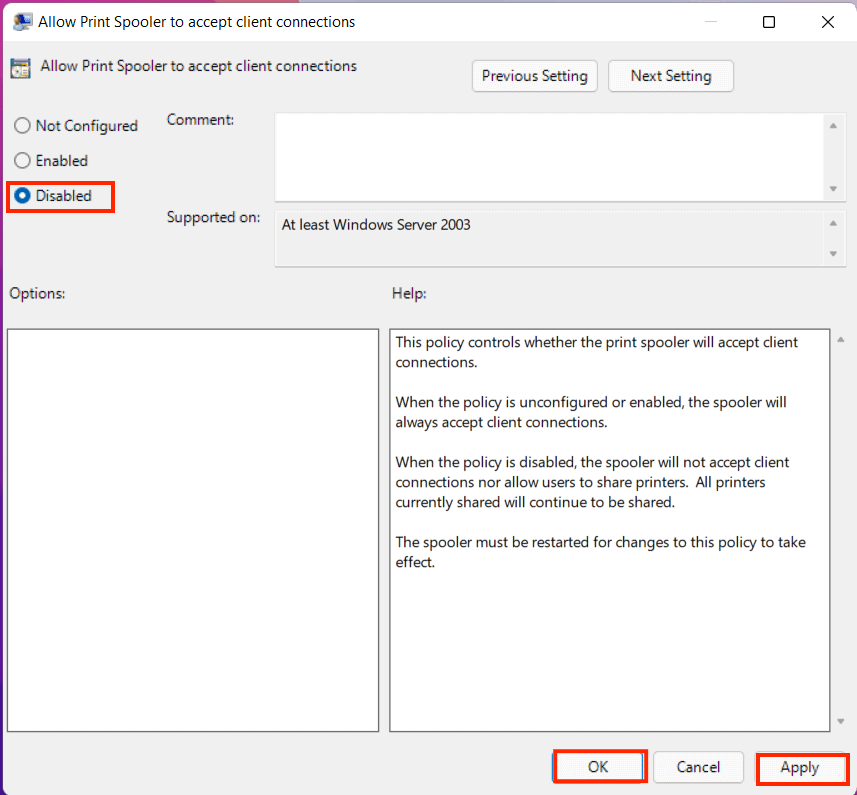
After disabling the Print Spooler service, it’s best to restart your PC to make the changes effectively. Once you restart, the Print Spooler service from your PC should get disabled completely.
How to Enable Print Spooler Service after the Printer Vulnerability Gets Fixed on Windows
Once Microsoft patches the Printer Vulnerability issue on Windows, you can re-enable the Print Spooler service to make your printer work again.
With Powershell:
Once the issue gets patched, you should re-enable the Print Spooler service, or else you won’t be able to print your documents or images from the printer locally or remotely if you used the Powershell method.
If you used Powershell to disable the Print Spooler service, here’s how to re-enable the Print Spooler service, once the Vulnerability gets patched:
- Open the Start menu, and search for “PowerShell.”
- From the right side options or by right clicking on “Windows PowerShell”, select Run as Administrator

- Type the first following command in PowerShell, and press the Enter key.
Set-Service -Name Spooler -StartupType Automatic - Then, enter the second following command in the Powershell window, and press the Enter key.
Start-Service -Name Spooler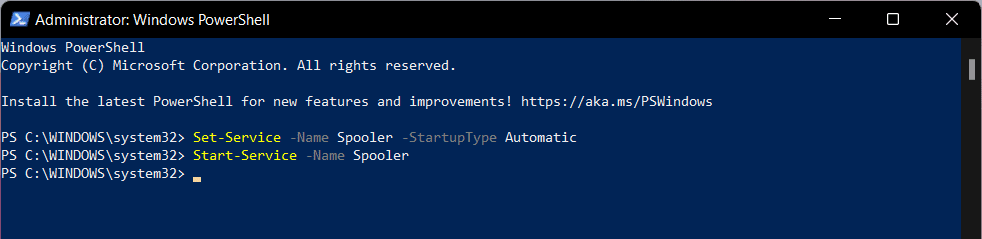
- Restart your PC for the changes to take effect.
These two commands will re-enable the Print Spooler service on your computer. Now you can print your documents again from the printer locally and remotely.
Also Read: How to Force Delete a File or Folder That Can’t be Deleted on Windows
With Group Policy Editor:
Once the issue gets patched, you should re-enable the Print Spooler service, or else you won’t be able to print your documents or images from the printer remotely if you used the Group Policy Editor method. Even if you don’t need to print remotely, it’s best to re-enable the service for your PC to keep it functioning smoothly.
If you used the Group Policy method earlier, you can use the following steps to re-enable the Print Spooler service after the vulnerability gets fixed.
- Open the Start menu, and search for “gpedit.msc” term.
- Click the Run as Administrator option from the right-side of the Start menu. If Run as Administrator is not available in Windows 11, you can click on the Open.

- Navigate to the Computer Configuration > Administrative Templates > Printers.
- Scroll and double-click on the “Allow Print Spooler to accept client connections”.

- Select the Not Configured radio button.
- Click Apply.
- Finally hit OK button.
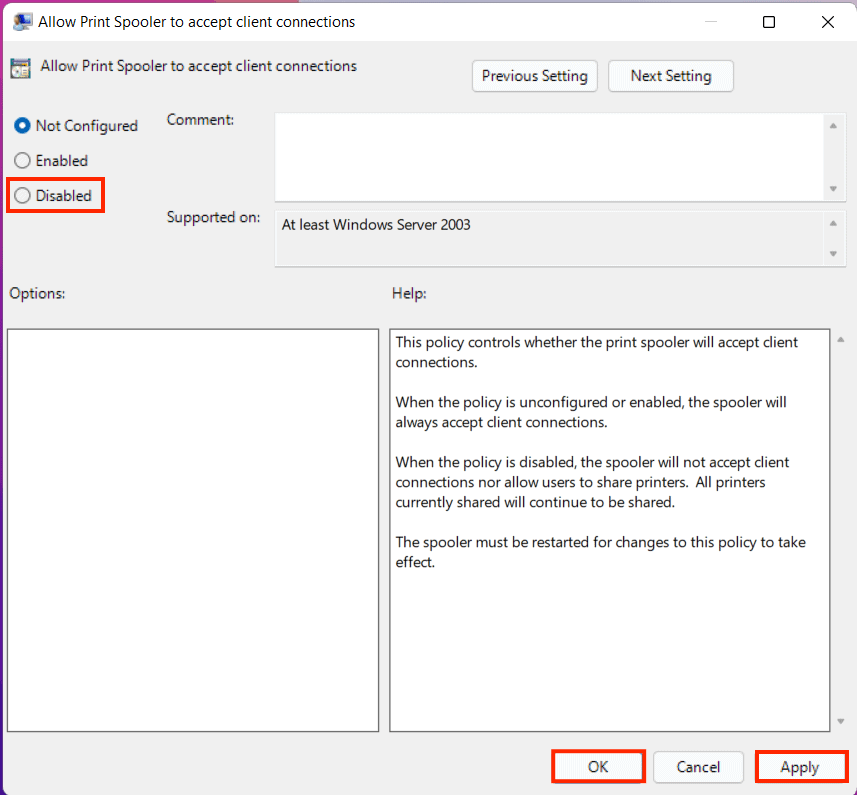
- Restart your PC for the changes to take effect
This should re-enable the Print Spooler service on your Windows PC, and you can now again print anything locally and remotely.
Also Read: How to Download and Install Canon LBP2900B Printer Drivers on macOS Mojave
Toggle Print Spooler Service When Required
Make sure you re-enable the Print Spooler Service with the same method you disabled it. If you used PowerShell to disable the Print Spooler, you have to only use PowerShell to re-enable it. The same applies to the Group Policy Editor method too.
If you are using the printer only for offline usage, you should consider using Group Policy Editor to stop Print Spooler Service. However, if you use both locally and remotely, toggle the service with the PowerShell method whenever required to stay safe and protected.
We hope you were able to follow the steps above to disable and enable the Print Spooler service on your PC. This is the only workaround to the ongoing Print vulnerability on Windows. Thus, until Microsoft releases a patch to this vulnerability, you should be using this workaround to stay safe from hackers.
This is just like the previous PrintNightmare Vulnerability, and right after that, Microsoft asked us to update our PCs with the latest security patches. Similarly, we’ll probably see a similar note from Microsoft once the vulnerability is patched. Until then, you should keep your Windows device safer by disabling the Print Spooler service.
