Uniqueness is one of the most important attributes of a password along with its length and the diversity of characters. Common passwords lack uniqueness, hence, they are fundamentally weak. It is important to note that common passwords also include passwords that are derived through common formulas or patterns. These passwords make the job easier for brute force attackers, and automated password guessing algorithms.
This post will discuss common passwords and password patterns, why they are risky, what password practices individuals should follow, and password habits they should avoid.
In this Page
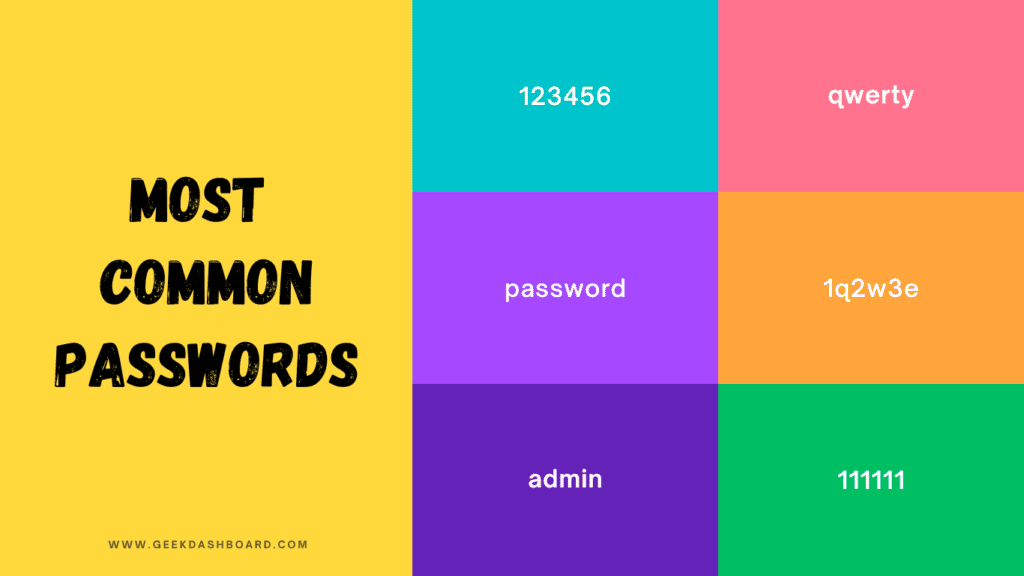
List of Most Common Passwords in 2025
- 123456
- 123456789
- qwerty
- password
- 12345
- qwerty123
- 1q2w3e
- 12345678
- 111111
- 1234567890
- admin
The list above is alarming because it showcases a severe lack of regard for password security. These passwords present little to no resistance against a password-cracking attack. Out of more than 15 billion stolen passwords analyzed by Cybernews, only a little over 2 billion passwords were unique. All the others were either common alphanumeric strings like the above or had easily discernible patterns.
Since these passwords are reused excessively, attackers can break into a large number of digital spaces simply by trying these passwords with stolen email IDs or user names.
4 Common Password Patterns
Internet users have the propensity to create passwords that are hard to guess for them (humans). In the process of creating strong passwords, they end up creating passwords that are easy to guess for computers.
Attackers use powerful automated tools that try all possible combinations of letters and characters to guess the right password. This is a resource-intensive process and has its limitations. A 12-character password consisting of a random collection of numbers, letters, and special characters, is almost impossible to guess through a brute-force attack.
However, the tendency among internet users to incorporate typical patterns in the passwords for their online accounts narrows down the parameters of a brute-force attack significantly improving its odds.

1. Sequential numbers and repeating characters
Sequential numbers starting from 1 or 9 are extremely common and passwords as such can be cracked almost instantly. Repeating the same number multiple times to create a passcode is equally fruitless owing to the commonness of such patterns.
2. Keyboard patterns
Users often tend to use keyboard patterns such as “asdfg”, “qwerty”, or “ghjkl” as passwords. Since these passwords are easy to visualize, they are also easy to remember. However, these too are common patterns and a computer will instantly crack these.
3. Common words, simple variations, and reverse words
Users often use words like “password”, “admin”, or phrases like “letmein” as their security code. Some create a new password by adding a simple variation to an already-used word, like “p@ssword” for password, or “53curity” for security.
In some cases, users type the words in reverse, for instance, “nimda” for admin or “koobecaf” for facebook. All of such patterns are common and attackers have large lists of such popular words and their variations. Hence, these codes cannot survive a dictionary attack.
4. Names and birthdays
Names, birth dates, pet names, names of the alma mater, and the brands a person has worked with, all can be easily scraped from social media or gathered through social engineering attacks. A person who likes to formulate their passwords by combining these elements might come up with a string like “Alex1990@hArvard”. While this is not as easily crackable as the previous ones, with the right set of information at hand, an attacker will get to it.
These aside, there are other patterns and features that attackers look for in a password. For instance, the year 2010 has been used in over 10 million passwords followed by “1987” which appeared in 8.4 million passcodes. Users also like to use the name of their favorite sports team, city, or hometown in a password. That is also something that narrows down the hunt for attackers.
How a Common Password is Guessed by an Attacker?

Here is an example of how a common password or password pattern makes the job easy for an attacker and how bad password habits put a user in deeper trouble.
The Premise
Alice is a tech-savvy individual with a lot of online accounts, However, she uses the same password, “Alice1990” across multiple accounts.
Now, one of the online services she uses faces a data breach and attackers get their hands on all the passwords. Nevertheless, the passwords were encrypted and therefore, the attackers got them in a hashed form. That means instead of the passwords in plaintext, the attackers have alphanumeric strings that represent the password.
The Challenge
In order to break into an account, the attackers need to guess a plaintext password that produces the same value as a password in the breached database when put through the hashing algorithm.
The good thing about hashing is that it’s a one-way process. The bad thing about hashing is that it produces the same hashed values for identical plaintext entries.
A Recognizable Pattern
In order to successfully crack a password, the attackers need to choose an easy target. This can be done by recognizing patterns. Common password patterns are reflected in the hashed values. Hence, when the attackers see the hashed value for “Alice1990” they recognize a pattern – a name + a year.
The Attack
The attacker uses a list of common names and years between 1980 and 1990 (they might select the range of years based on the typical user demographic of the software they breached) to narrow down the brute force.
Now, the automated tool tries each combination of names and years from the list until there is a match between the resultant hash and the targeted hash. Once a match is found, the attacker gets the password – Alice1990 and logs into her account.
The Escalation
With access to the password Alice had reused everywhere, the attacker gained access to all her digital accounts including professional accounts. This could result in a breach of sensitive data, and financial and reputational loss, among other things.

This is how common password mistakes can result in major setbacks and life-altering events. With a more secure password, something with at least 12 characters and no recognizable patterns could have saved Alice. If she had set different passwords for each account, the attackers wouldn’t be able to escalate the attack so easily.
3 Secure Password Practices to Follow
Uniqkey, a specialized tool for managing business passwords, has created a helpful guide on ‘password management strategies‘. This guide provides businesses with useful tips and practical advice on how to manage passwords more effectively. Additionally, you can also start implementing some basic practices right away from below to improve your password management.
- Do not use easily guessable passwords: If you want something memorable, use a long phrase that doesn’t have common patterns. It can be something important to you but not a simple collection of items that are easily imaginable.
- Do not share passwords in plaintext: Your passwords are kept in a database as hashed values. But when you share them in plaintext they are easily accessible through interception of the communication medium.
- Use a password manager: A password manager generates unguessable passwords for you, encrypts them and stores them, and auto-fills your credential fields. It takes the hassle away from the entire process of authentication.
