The term ransomware isn’t new to even an ordinary computer user, thanks to the widespread WannaCry attack. People came to know it is possible to remotely control software to encrypt files and ask a ransom for decrypting them.
It looks like the attackers want to take many computers down and make some money. Another ransomware self-named Bad Rabbit is buzzing in the cybersecurity field now.
Bad Rabbit Ransomware Hit Russia and Spread around the Globe
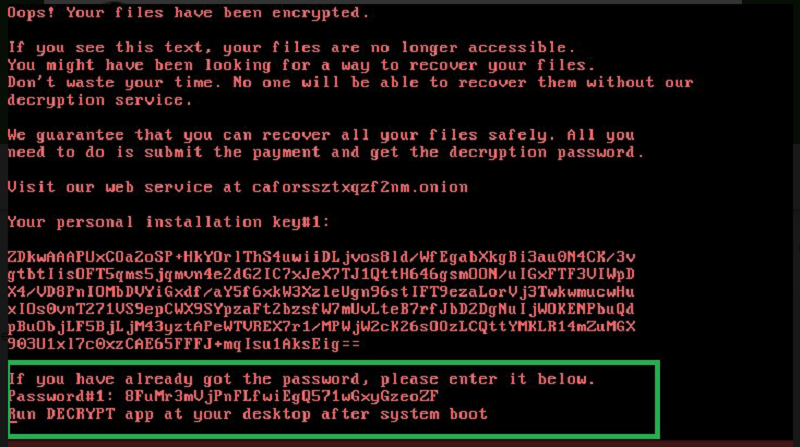
Ransomware first encrypts important files on computers and asks for money in bitcoin for decrypting them. The new one, Bad Rabbit infected servers, and computers in Ukraine and Russia. Bearing similarities to the NotPetya attack (caused damage in billions), the new one demands a payment of 0.05 bitcoin (worth $250) for the decrypting key.
Also Read: How to Remove Cryptolocker Ransomware and Decrypt your Infected Files
The ransom amount is similar to what we see with the attack in June and the Kaspersky security firm says the methods are also similar to that of the NotPetya.
Kiev’s metro system, Russian media organization Interfax and Odessa airport are in the list of affected agencies. Interfax’s server went offline for a few hours that they had to publish the news on their Facebook page.
Cybersecurity experts dug into the codes of the ransomware and found the references to the names of two dragons in the blockbuster TV series Game of Thrones. Malware tries four common passwords (“love”, “sex”, “god” and “secret”) while trying to sneak into a system. The 1995 movie Hackers used the aforementioned four words the most.
Kaspersky researchers observed that the attack targets corporate networks. The servers used as the secondary channel for the distribution of Bad Rabbit were the ones used in NotPetya attack for spreading the initial compromised software.
NotPetya’s target was Ukraine on the contrary to Bad Rabbit’s, which is Russia. Moreover, the new ransomware isn’t a wiper. When you enter the correct key, it decrypts every single encrypted file. On the other hand, NotPetya remained in the host to create other fetal damages.
Bad Rabbit enters into a computer mostly via a fake Adobe Flash Player update notice. It doesn’t use any tricks to make you open as the notifications seem so real that the user does it him/herself.

Want to secure your system even without an antivirus? Then, go to C:Windows and create a file with the name infpub.dat and cscc.dat. Don’t forget to remove all write permissions of it.
What do you think of the Bad Rabbit ransomware? Are you safe from such threats? Let us know in the comment section below.

such a great post thanks for sharing..